If you are interested in the cryptography in Bitcoin take a look at this short article (remember that BTC have moved from ECDSA to Schnorr signatures).
This leads me up to another article I have started to write.
If you know nothing about cryptographic, read some books about it. It´s super fascinating stuff.
Let me give you a small timeline of some methods for hiding secret messages, remember there are also tons of nice algorithms you can use on your computer:
405 BCE – The Ancient Greek general Lysander of Sparta is said to have received a message which was revealed by winding a piece of parchment around a rod of a special thickness – This is known as a scytale.
50 BCE – Julius Ceasar did not invent it, but used it a lot. It´s called Ceasar ciphers. A simple way to disguise messages by replacing each letter with another. This is the basis for many more complicated ciphers.
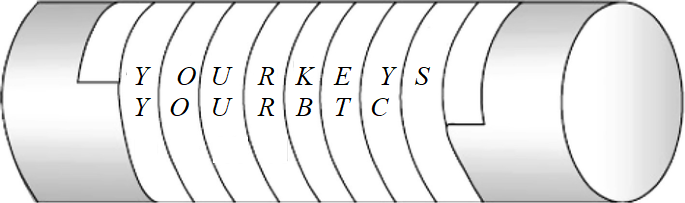
An example of a cipher wheel:
- The key is 8 and I have rolled (turned the inner wheel eight places clockwise) it for you.
- Find this secret message: OMB I TV EITTMB
- Look at the red outer wheel and start to decode.
- Write down the matching letter from the inner wheel.

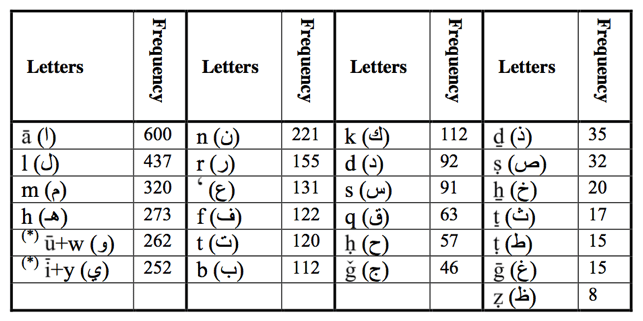
850 CE – al-Kindi an Arab scholar and mathematician was the first person to describe a method to decipher encrypted messages based on how often letter are used in a language, also called frequency analysis
1800s CE – As the global electric telegraph network grew in 1800s, so did the use of codes and ciphers. Before that it was mostly by hand and pen.
Pocket cipher machines was also seen in this periods, like the one made by Decius Wadsworth (1817) but popularized by Sir Charles Wheatstone.

Military started also to use these handheld systems, like the Pletts wheel (first world war), but it was fast rejected by the British army after American codebreakers (E. and W. Friedman) fast broke it.

1900s CE – Mechanical gear-and-rotor cipher machines began in the early 1900s. This really sped up encryption in an age when messages were sent around the world via telegraph cables and radio communication.
First world war proved that secure messages by mechanical gear-and-rotor cipher machines saved lives.
1908-1924 CE Example of a experimental cipher machine (Sir Perry Scott’s cipher machine 1908)

The flawed insecure Kryha Machine (1924).

1923 Ce Electric typewriter – The Famous Enigma machine protected commercial, diplomatic, and military communication in Nazi German broken by famous Alan Turing (Bletchey Park) with the help of French secret service and the Polish Cipher Bureau.

1930 CE – T52 was an online machine used by Luftwaffe and German Navy units, which could support the heavy machine, teletypewriter and attendant fixed circuits. Broken by Arne Beurling.

1937 CE – Electric typewriter TYPEX an adaptation of the commercial German Enigma with a number of enhancements that greatly increased its security.

1936-1940 Portable cipher machines like the Hagelin C-36.

1940s CE – The Lorenz company designed a cipher machine based on the additive method for enciphering teleprinter messages invented in 1918 by Gilbert Vernam in America. The Lorenz machine was often used for the most secret messages.
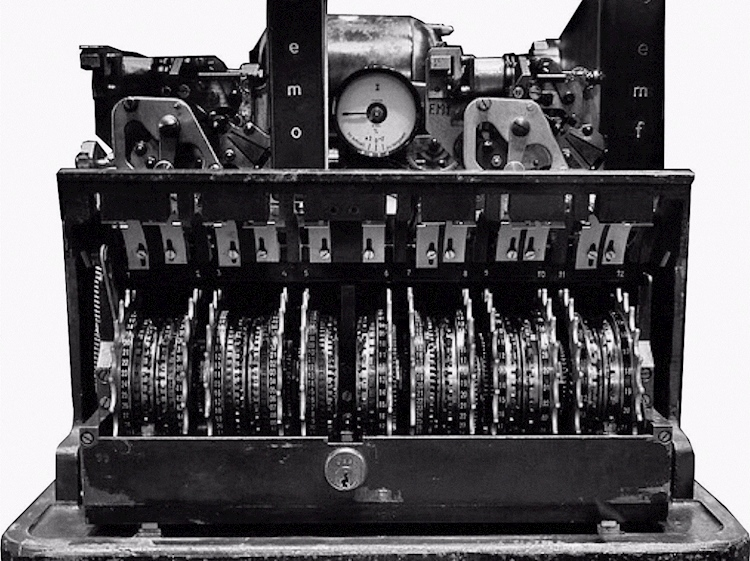
1941 CE – The SG-41 or Hitler mill troubled many in Blechley park.

After this period many machines were produced but here are a few of them.
1943 CE The 5-UCO or BID/30 was an electronic One-Time Tape (OTT) cipher machine, or mixer, developed in the UK during WWII and used for Top Secret Ultra messages during the war. After the war, the machine was used by the British Commonwealth, the US and NATO. The machine was suitable for fully synchronous secure telegraphic data over the HF radio bands.

1962 CE – AVLIS or BID/610 was a fully transistorized online/offline cipher machine, introduced in 1962 by Plessey in Liverpool (UK). The machine was used by British and Canadian forces and also by NATO. It was the UK’s submission for NATO evaluation TROL and was approved on 17 April 1962 for NATO information of all classifications, including TOP SECRET.

Read here a fun/tragic story about the last rotor cipher machine.
1960s CE – Delphi punch-card cipher machine was the first machine to have the key (Usually strong random number) encoded on punch cards.

2000s CE – Thamer a commercial available technology that connects to personal computers in order to encrypt classified data traffic.

Chaotic pendulum and Lava lamps are seen used by some companies to create random numbers.


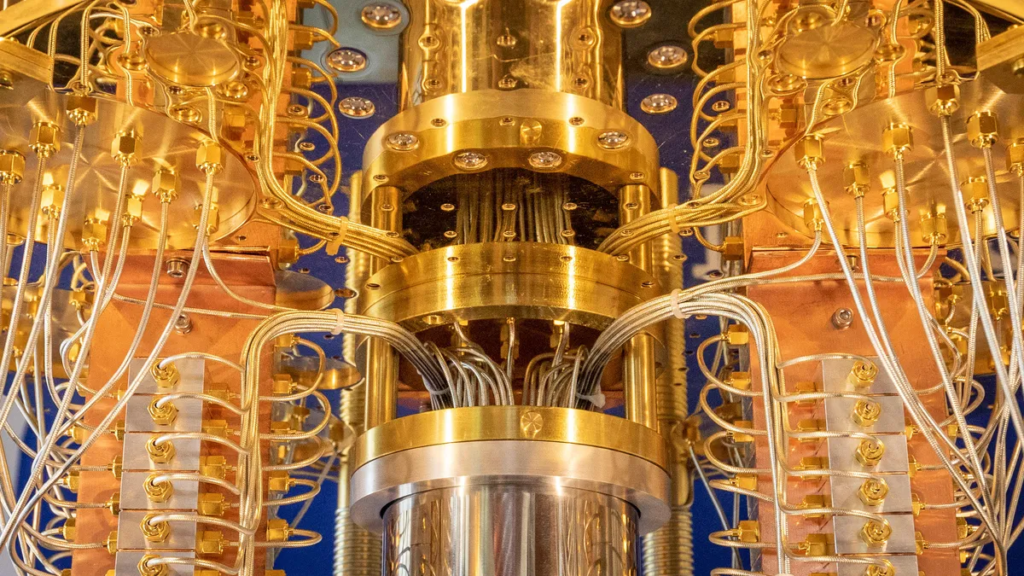
Now and the future – Quantum computers are able to break some of today´s encryption methods in seconds, but they also open up for the future of encryption technologies.
I hope you liked this post; I have travelled around to see some of these technologies IRL. But there is a lot more to all this, but why reveal it all – You got to have some secrets:D
By the way you should read about Gottfried Wilhelm Leibniz his findings have been used in so many things in todays society, but it´s about to change.
AN OVERVIEW OF BITCOIN’S CRYPTOGRAPHY
Secret dust pooof – I am out!
Powered by BTCPayWall