
Bitcoin has several attack vectors that can be exploited by a quantum computer.
Various algorithms, such as Shor’s algorithm (for integer factorization) and Grover’s algorithm (Search), pose significant threats to the Bitcoin protocol. These algorithms can potentially enable cryptanalytic (brute-force) attacks on different aspects of the known protocol.
I can identify three areas with vulnerabilities in the long run, and the communication layer, which is currently in the process of being addressed:
- Mining Bitcoin
- Wallets (Public Key Cryptography)
- Lightning Network Data
Mining
Bitcoin employs the Nakamoto consensus, which includes Proof-of-Work (PoW).
Miners compete to earn block rewards by discovering nonces (hash values less than or equal to the target). Each block, with a block time of 10 minutes, contains a nonce and a block reward.
The PoW function utilizes SHA256^2, which could be susceptible to attacks in the future. It could be conceivable to utilize Grover’s algorithm for precomputations and hash discovery. You can review the setup in this paper and here.
Various proposals have been put forth to enhance the security of the PoW function. One idea is transitioning from SHA2 to SHA3, although this would effectively render the currently used ASIC mining hardware obsolete.
Alternatively, changing to a different quantum-safe PoW protocol is another option.
As of now, breaking SHA256^2 is not possible since quantum computers require more qubits for such an operation.
Wallets
First, it is important to understand how a wallet is constructed.
One common example is the P2PKH wallet.
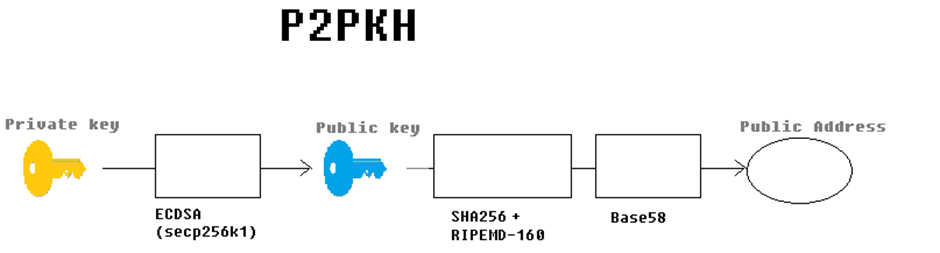
Figure 1 – How a P2PKH wallet is created
a. Bitcoin uses ECDSA to derive a “public key” from the private key (a 256-bit number).
b. Next, the public key undergoes hashing using SHA256.
c. Following that, RIPEDMD-160 is applied.
d. The resulting output is converted using Base58 encoding.
e. Now, a public address is ready for use.
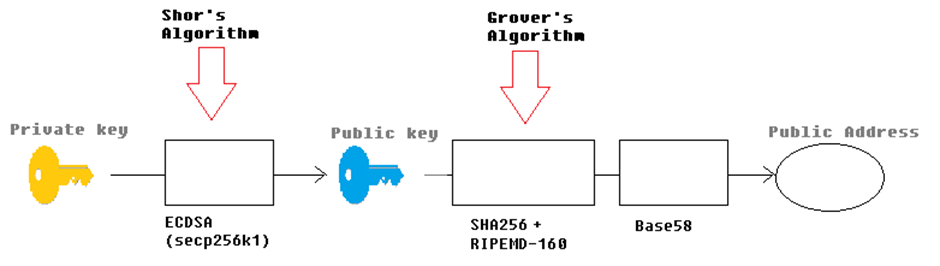
Figure 2 – Possible attacking vectors:
- RIPEMD-160 (hash function) attacked via Grover’s algorithm
- SHA256 (hash function) via attacked via Grover’s algorithm
- ECDSA attacked via Shor´s algorithm
It is currently not feasible to brute-force P2PKH since quantum computers require more qubits for such an operation (https://pubs.aip.org/avs/aqs/article/4/1/013801/2835275/The-impact-of-hardware-specifications-on-reaching).
Various proposals exist to enhance the security of private keys. These include transitioning from SHA2 to SHA3, using algorithms such as CRYSTALS-Kyber, employing x.509 certificates, and adopting Falcon 512 or less secure Lamport signatures. You can find further details here (https://par.nsf.gov/servlets/purl/10324007) and information about attacks on RIPEMD-160 and SHA256 here (https://eprint.iacr.org/2023/285.pdf).
Additionally, you can explore the NIST candidates for post-quantum cryptography here (https://csrc.nist.gov/Projects/post-quantum-cryptography/selected-algorithms-2022).
It’s important to note that there are various BTC wallets with different public key encryption techniques, including alternative forms of encryption like Schnorr (P2TR) and some with less reliance on hashing functions like (P2PK).
Even though wallets use different techniques to generate addresses, all of them can potentially be compromised using the same algorithm employed for brute-forcing P2PKH.
Additional Information: The various mainnet wallet types can be distinguished by their addresses. Some start with 1, 3, bc1, or bc1p, while testnet addresses typically begin with m or n.
Lightning Network Data
The Lightning network employs the Noise protocol (http://www.noiseprotocol.org/noise.html), which is fundamentally based on Diffie-Hellman key agreements.
It would theoretically be possible to use Shor’s algorithm to break this (Discrete log problem), potentially allowing access to historical communications between Lightning Network nodes (I’m not entirely certain about this – Not much research about it?).
Currently, brute-forcing the used Diffie-Hellman key agreement in Noise is not feasible, as quantum computers require more qubits for such an operation.
There are various proposals, such as upgrading to CRYSTALS-Kyber, to enhance security.
Communication Layer (Privacy Update)
The communication (P2P) layer is currently transmitting messages without encryption. This needs to be updated to implement opportunistic encryption between nodes to address issues related to censorship, privacy breaches, and other potential attacks.
This update will be achieved through the use of BIP324 (https://github.com/dhruv/bips/blob/bip324/bip-0324.mediawiki) and ElligatorSwift (https://eprint.iacr.org/2022/759.pdf).
Considerations:
Currently, Bitcoin remains resilient against cryptanalytic attacks launched by quantum computing, thanks to the absence of practical quantum algorithms capable of breaking its security.
Bitcoin employs various algorithms with different security levels, each offering varying degrees of resistance to cryptanalytic attacks.
One factor to bear in mind is Bitcoin’s bandwidth, which serves as a limiting factor. Some of the proposed algorithms may require more memory per key, potentially affecting network performance (source: https://eprint.iacr.org/2021/781.pdf).
Bitcoin has the capability to implement new security standards through BIPs (Bitcoin Improvement Proposals), a process that has occurred multiple times throughout Bitcoin’s history (source: https://github.com/bitcoin/bips).
It’s important to acknowledge that this transition process takes time and can be met with significant controversy and resistance regarding BIP adoption rates. Therefore, the migration time to more secure standards should be carefully considered in light of the evolving threat landscape posed by quantum computers.
Note: While I don’t have formal education in cryptography, I’ve tried to provide some suggestions, and there are likely better ideas available for improving the Bitcoin protocol. There are still many years until it’s needed, but it’s always prudent to survey the landscape.
Tip: Use a Bitcoin address once and then change it. Most wallets let you generate new addresses after each transaction. Read more about keys and wallets here.
Powered by BTCPayWall